X-FRAME-OPTIONS
This X-FRAME-OPTIONS HTTP header invented by Microsoft for IE8 provides an easy way to work around Clickjacking security issue (see this great paper for even more details). The main article explaining how X-FRAME-OPTION works is this: http://blogs.msdn.com/b/ie/archive/2009/01/27/ie8-security-part-vii-clickjacking-defenses.aspx
Basically, here’s what behaviour you get with different X-FRAME-OPTIONS values:
| `DENY` | browser will not render the iframe contents in any case |
| `SAMEORIGIN` | browser will only render the iframe contents if host page origin is the same as the iframe page origin |
| `ALLOW FROM http://host` | browser will only render the iframe contents if the iframe host is httр://host |
Please note that specifying the header in META tag won’t work.
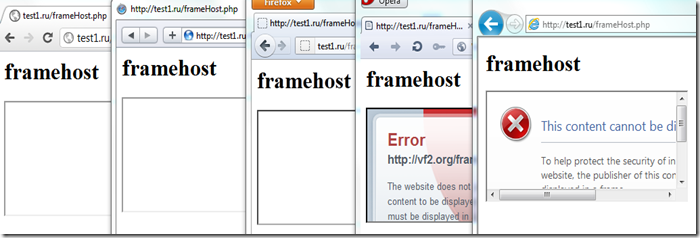
Good news – all browsers vendors copied this from Microsoft and now we’ve got all modern browsers supporting this header (Firefox 3.6.9, IE8, Opera 10.50, Safari 4.0, Chrome 4.1).
Unfortunately, for some reason only Opera and IE show a meaningful message why the frame was blocked, all others just display the empty iframe (it’s especially weird for Firefox, which should show the warning as per their bugzilla):
In any case, study the security papers I linked to above to understand how the attack works and what it can do to your visitors or your business.
However, if you strongly believe no one should embed your page in an iframe – then your silver bullet is to add X-FRAME-OPTIONS: DENY to all the pages you serve.
P.S. X-FRAME-OPTIONS is now proposed to IETF: http://tools.ietf.org/html/draft-gondrom-frame-options-01